Opinion
Does Public Diplomacy Matter?
Introduction
We hear about ‘public diplomacy’ virtually on a daily basis as if it has been around forever but as a matter of fact, this precise term is only circa 50 years old, having been coined in 1965 by Edmund Gullion. In what follows, I will make an attempt at clarifying the meaning of this notorious notion and at understanding it significance in contemporary international affairs.
My proposition is to set a distinction between two forms of public diplomacy, only the first of which will then be analysed under the meaning/content, and relevance aspects. The first type I label as ‘top-down public diplomacy’, which contrasts with the second type, ‘bottom-up public diplomacy’.
Before going into more detail, I want to make a general assessment of the topic. The whole business of diplomacy can be considered as representation and communication. Public diplomacy goes even further into influencing the ‘public attitudes on the formation and execution of foreign policies.’ By ‘top-down’ I am referring to a relation of communication or influence that has a national government (state) as the transmitter and the general public (non-state) as receiver. ‘Bottom-up’ I conceive to be exactly the opposite, a relationship that reflects the communicative and influential input of the public for achieving a certain political output from a government. This can be done either directly, public – foreign government, or indirectly: public – foreign public – foreign government.
Top-down public diplomacy
This typology of public diplomacy refers to all the actions that a government takes to communicate to foreign publics and influence their thinking and behaviour. Also, the spread of a good image of the country worldwide is a task of public diplomacy. What sort of actions do governments undertake in this sense?
A first one could be the direct address by high officials. Representative is George W. Bush’s speech on the war on terror. He thanks ‘on behalf of the American people…the world for its outpouring of support’. His recipients are not foreign government officials, but the general foreign public made up of ‘South Korean children gathering to pray outside our embassy in Seoul’, others who pray in the ‘mosque in Cairo’, and those who kept ‘moments of silence and days of mourning in Australia and Africa and Latin America’. Bush addresses through this speech the Taliban openly, asking for the release of foreign nationals and the delivery of Bin Laden. He also speaks ‘directly to Muslims throughout the world’, claiming to respect their faith. Even though President Bush is only talking to his immediate audience, the Joint Session of the 107th Congress, he is in fact aware that the whole world is watching. He is holding a one-way ‘diplomatic meeting’ with the foreign public via media broadcasting.
One more instrument of public diplomacy is the spread of governmentally-funded NGOS and foundations around the globe with the aim to endorse the image of the country of origin, its values, and to facilitate the execution of foreign policy by preparing foreign audiences into being more receptive. One illustrative example is the Romanian Cultural Institute, which has the mission to promote ‘national culture and civilization in Romania and abroad’, therefore acting as a ‘crucial complementary instrument’ for achieving ‘Romania’s strategic objectives’. Its work is structured around a number of ‘programs, project, and activities’ which mainly focus on identity issues like language, traditions, and artistic and intellectual creations. This case fits more with the prestige of a country function of public diplomacy. States like Romania and Bulgaria who have been admitted lastly into the EU, could benefit from this kind of tool to approach an EU public that has been since critical of the last wave of enlargement ever since it started.
What about the relevance of public diplomacy ? I would argue positively. Both from the theoretical perspective and from the practical side. Regarding the conceptual relevance, this notion of public diplomacy manages to explain a behaviour that would in its absence be harder to grasp. Why would President Bush address people who are not present in the room while holding his speech? Was it merely rhetoric for influencing the members of the Congress and for getting into the graces of the American people? It is more. I would argue it is part of a larger diplomatic effort meant to build up that coalition of 49 countries willing to participate in Operation Iraqi Freedom. The participation to the war in Iraq can be justified by a feeling of empathy to the American sufferings of 9/11 and by a fear of terrorism, both instilled in the foreign audience initially by Bush’s public diplomacy.
On a practical level, public diplomacy is very relevant in the age of globalization and under the dominance of a liberal/democratic international order because state actors’ actions are under more scrutiny. Legitimacy is a higher priority. The amplification of global interaction together with the impact of Internet and social media leads to more interdependence, which in turn distorts the line between domestic and foreign policy. When a Christian fundamentalist burned the Qur’an in the US (2011), the Muslim world immediately reacted: this event transgressed boundaries from a domestic event into a foreign policy instance. A confined episode turned into a threat to US reputation. Respectable reputation along with legitimacy revolves around the idea of soft power, a vital ingredient for decreasing hostility and earning the confidence vote to lead internationally.
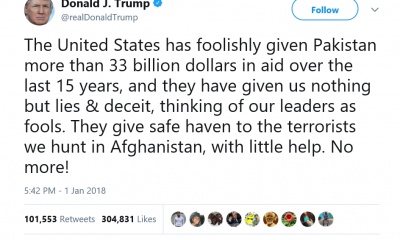
The international legal order is constructed today on the basis of the UN Charter. The United Nations is officially the main source of lawfulness and legitimacy on the world scene, argument proved by the intention of Palestine to be recognized by the UN as a member state. A current affairs instance of the role of international law is the Russian annexation of Crimea or the unification of Crimea to Russia, depending on the political position. Article 1 and Article 2 offer different decisions to whether this situation was legal or not. Namely, the right to self-determination of the Russians in Crimea against the right to territorial integrity. Political legitimacy also plays a part in this debate: was the interim government legitimate or not? Regardless of the answer, what matters is that the debate around international norms and principles sugar-coated realpolitik. Why? Because states need to be acting in accordance with what the public opinion sees as right, which in this case is prescribed in the UN Charter.
An overlooked characteristic of public diplomacy is its domestic variation, namely the engagement of the domestic public. The context of democratization in foreign policy-making is valuable in emphasizing the role of the local population in consenting to, embracing and disseminating the principles and goals of the national leaders in an environment where, as mentioned earlier, the boundaries between what is domestic and what is international are fading. Let’s take an example. The People’s Republic of China is established under the ‘people’s democratic dictatorship’. The domestic facet of the public diplomacy in this country has the exact target of promoting the principle of ‘governing for the people’ in foreign matters as well, and it is implemented through constant interaction between the general public and the foreign ministry (conferences, online discussions, visits).
Conclusion
To sum up our discussion, we can positively affirm that public diplomacy is relevant in contemporary international relations due to a number of characteristics of the global arena. These are:
- the states’ need for legitimacy both from the foreign public and domestic one;
- the higher role of reputation and soft power;
- the requirement to be compliant with international law which makes states justify their actions to the public;
- high global interaction and access which leads to more scrutiny of state actions:
- an ever more blurry line between domestic and foreign issues;
- increasing involvement of domestic constituencies in foreign policy-making both in democracies and illiberal states;
All these features determine states to consider the international public opinion in the process of decision-making, especially in matters of external affairs. This effort to communicate more, influence more, involve more, promote more to the foreign public complementary to foreign governments is the task of a public diplomacy that is here to stay.
List of references
(Tr.) Sultan C., April 18, 2005, Europe Union: How Fit Are Romania and Bulgaria for the EU?, at Spiegel.de, website: http://www.spiegel.de/international/spiegel/europe-union-how-fit-are-romania-and-bulgaria-for-the-eu-a-352874.html ;
Armitage R, Nye J. (2007), CSIS COMMISSION ON SMART POWER. A smarter, more secure America, CENTER FOR STRATEGIC & INTERNATIONAL STUDIES, The CSIS Press, Washington DC;
BBC.com, 30 November 2012, Q&A: Palestinians’ upgraded UN status, website: http://www.bbc.com/news/world-middle-east-13701636 ;
Carlsnaes W, Risse T., Simmons B. (2002), Diplomacy, Bargaining and Negotiation, in Handbook of International Relations, pp. 212-235, SAGE Publications Ltd;
Constitution of the People’s Republic of China (2004), website: http://www.npc.gov.cn/englishnpc/Constitution/2007-11/15/content_1372963.htm ;
Kerr P., Wiseman G. (2013), Diplomacy in a globalizing world. Theories and Practices, Oxford University Press;
Operation Iraqi Freedom, March 27, 2003, at whitehouse.archives.gov, website: http://georgewbush-whitehouse.archives.gov/news/releases/2003/03/20030327-10.html ;
The Fletcher School and Law and Diplomacy, Tufts University (2014), What is Public Diplomacy, website: http://fletcher.tufts.edu/Murrow/Diplomacy
China
Nepal Hindu Rashtra: Time to Wrap Up Communism?

Nepal abolished the Constitutional Monarchy in May 2008 and declared itself as a Federal Democratic Republic. There was a new hope in Nepal as it was becoming world’s newest democracy even though it had dissolved the Hindu Rashtra. However, the democracy in Nepal immediately got into the tight grips of leftists and communists backed by China. It has been almost 12 years since monarchy was abolished in Nepal. Interestingly, the Himalayan country has already seen 11 Prime Ministers in this period. Thus, leaving the Nepalese people still yearning for good and stable governance.
Re-establish Hindu Rashtra
As the political instability is growing in Nepal, people are demonstrating concerns about the future of the country. In fact, Nepalese citizens are unhappy with frequent interference by China and India influencing its unstable communist regime. More voices are now growing in support of reinstating the Monarchy and declaring Nepal as world’s only Hindu Rashtra (which by default offers full religious freedom to other religious minorities as per Hindutva concept of Sarva Dharma Sama Bhava – all paths lead to one).
Former Deputy Prime Minister of Nepal, Kamal Thapa said that if political parties do not recognize the seriousness of reinstating the monarchy, then the country will head for a period of darkness. “Recently, we’ve had high-ranking officials from India and China come to Nepal to try and solve problems within the ruling party,” he said. “We cannot let others dictate what we want to do.”
Communist Party All Set to Suppress Protests, By Force
Kamal Thapa has firmly demanded an all party meet to discuss reinstating of monarchy. Throughout the month of December, 2020 Nepal has seen anti communism protests across the country in support of reinstating the monarchy and Hindu Rashtra. Most importantly, the demand has become a nationwide mass people’s movement. So much so that the communist regime had to send a directive to 77 districts in 7 provinces. The directive suggests suppressing the protests by force. Nevertheless, Rashtriya Prajatantra Party and other royalist groups have ignored this threat from the communist regime. Protester groups have pledged to strengthen the protest in the coming weeks.
Nepal: Demonstration held in capital Kathmandu, demanding restoration of monarchy in the country. pic.twitter.com/TFjmKu9U9Z
— ANI (@ANI) December 5, 2020
Role of China – Hope for Communism in Nepal
China’s ambassador to Nepal is known to have very close relationship with Nepalese Communist regime. In fact, She has been super effective in tilting Nepal’s posture towards its ideological partner, China. One of her greatest achievements in 2020 was artificially manufacturing a border conflict between Nepal and India. Consequently, souring relations between the two Hindu majority nations. In addition, she managed to silence Nepal’s communist government after China took one of Nepal’s border villages under its control. However, recent political turmoil in Nepal and a renewed demand for reinstating of Hindu Monarchy is showing that the situation is now out of Chinese hands
Role of India
Year 2020, was not a good year for India and Nepal relations. India was busy in controlling domestic Covid cases. On the other hand, China had launched an invasive campaign into Indian territory. In addition, India is always busy with Pakistan on its western borders. However, the surprise came to India when China was almost successful in creating a new border tension between India and Nepal.
Those who do not know about Indian government should note that the current ruling party in India finds itself ideologically opposite to communism. This further creates differences between the two countries.
Communist party in Nepal has blamed India for supporting the ongoing anti communism protests in Nepal. However, former advisor to Nepal’s PM has suggested there is no proof that India is fueling pro Monarchy, anti communism demand in Nepal.
Nevertheless, There are certain influencers in India who have, in their personal capacity, expressed support for reinstating the Hindu monarchy. Yogi Adityanath, who is the Chief Minister of an Indian state bordering Nepal, said in 2015 that Nepal should declare itself a Hindu Monarchy. Readers should note that in 2015 Yogi Adityanath was not the Chief Minister yet. However, today he is not only popular in south of Nepal, his popularity is growing in Nepal as well.
Will The World See the first Hindu Rashtra?
It is difficult to answer this question at this moment. However, Nepalese communist government could not resolve the political instability and in December 2020 Nepalese government dissolved the parliament. Nepal will see next elections in April – May 2021. Hopefully, the world will see Nepal’s 12th Prime Minister in 13 years or may be a Hindu King? Royalists and protester groups have expressed confidence in winning next elections. We have our eyes on Nepal for updates.
Opinion
America’s Justice System – The Need For Reform

A recent poll by the National Opinion Research Centre revealed that 95% of Americans favour vital criminal justice reforms. This is hardly surprising, given that several people of varying racial, partisan and ideological dispositions have called out the justice system over its many failures throughout the years. Most Americans received the Trump Administration’s First Step Act as a step in the right direction, as about 60% of people approved the criminal justice reform bill according to a 2018 poll. However, many people still believe the justice system’s approach to crime is ineffective and needs dire change, and these are some reasons why.
Prison population and funding concerns
Research conducted revealed America has about 2.3 million prisoners, making the US the country with the highest incarceration rate globally. Experts estimate that the country’s prison population has grown by a whopping 340% over the past three decades; new prisoner admissions into jails are higher than prisoner release numbers. The cost of maintaining the nation’s prisons at taxpayers’ expense has inspired a lot of backlash and calls for budget cuts. According to research, slashed correction spending was the preferred option by most states to balance their budgets and redirect spending to other areas.
Minimum mandatory sentences
Minimum mandatory sentences are statutes that force judges to give defendants convicted of a crime the minimum prison sentence. Mandatory sentences rob judges of the traditional way of considering the defendant’s character and the unique circumstances surrounding offences. Even when represented by criminal defense attorneys with many years’ experience, defendants often succumb to prosecutors’ pressure to plead guilty or face more severe charges with higher mandatory sentences. The guilty plea bargain consequently resolves about 95% of both federal and state court cases. Research also shows that about half of inmates in federal prisons are doing time for drug offences- causing overpopulation in the prison system.
Growing number of people killed by the police
An estimated 1000 civilians are killed by police officers annually in the US. The frequency of police brutality cases over the years requires immediate reform to the American justice system. Data suggests that the incidence of fatal police shootings is higher among African-Americans than any other ethnicity, inspiring movements like the ‘Black Lives Matter’ campaign to press on with protests for significant police etiquette reforms towards coloured minorities. The police force faces incessant accusations of racial profiling, indiscriminate use of power, and poor discretion, which has led a reported 58% of Americans to think policing needs major reforms through measures like better-trained officers, and wearing body cameras.
Evolving public opinion on crime
Research released by the Sentencing Project and The Justice Policy Institute reveals that more people in conservative states are embracing preventive, rehabilitative, and alternative sentencing options for non-violent offenders. Most Americans now view the prevention of crime as the most vital function of the justice system, as 77% of Americans think that focusing more on character education and after-school programs would be cost-effective by reducing the number of people going to jail. Almost two-thirds of Americans also believe in the need for lighter sentences with more useful, reformative programs in prisons that will benefit inmates upon release. Therefore, support for harsh penalties that harden criminals and make them a more significant menace when reintroduced into society has dwindled.
Opinion
The History Question: Is It Better to Remember or to Forget?

Years ago, a philosopher by the name of George Santayana said a phrase that fuels many debates to this day. His original saying is “those who cannot remember the past are condemned to repeat it”, although, many sources now present it as variations of “those who cannot learn from history are doomed to repeat it”. The latter definitely has more substance to it in the light of the ongoing debate about how much history we should be learning and how.
Is It Better to Remember or Forget About the Past?
On one hand, Santayana was right. Learning about the past is essential in order for people to progress. One also shouldn’t overlook the importance of remembrance and paying respects to the dead, both those who pushed the progress forward and those who have fallen victims to major tragedies that could and should have been averted.
The main argument in favor of learning about the past is that its knowledge is necessary for preventing the same thing happening in the future. Having it one can see the signs and stop the tragedy before it gains momentum.
That’s sound in theory, but the reality is always different. For example, today people are surely forgetting, and the much-critiqued education system is only partially at fault here. Even the greatest of tragedies weren’t spared this fate. It’s a proven fact that about two-thirds of millennials today don’t know about the Holocaust, and this number is surely greater for generations that follow them. In the school history course, the subject of one of the greatest disasters in history is barely touched, if touched at all. And outside of a history classroom, one can only see small, but terrifying, glimpses of it at the Holocaust Museum and other museums that rarely attract many visitors. And now we are witnessing a rise of antisemitic crime.
Are these two facts related? Does the lack of awareness about the horrors done in the name of Aryan supremacy contribute to the fact that right-winged extremists seem to be gaining popularity again?
It does, but by how much? That is the question that no one can truly answer.
And what about other genocides? The Holocaust had the highest death toll, but it was far from the only genocide in history. And quite a few of those happened after World War 2 and before the memory of the atrocities against the Jews began to fade. This means that while forgetting history is a factor, it’s not the deciding factor in its repeats.
But what is that thing responsible for the reenactment of past mistakes and tragedies?
Learning. This is the important thing that is most often overlooked when citing Santayana’s famous saying. It’s not enough to learn about the past and know the facts of things that happened. It’s important to learn from those facts and put in place protections that will prevent them from happening again. And this is something that humanity, as a whole, has yet to succeed in doing.
Dwelling in the Past Can Be Just As Bad
One also shouldn’t forget that there is such a thing as “too much history”. The Bosnian War and genocide that happened there in the 1990s is a vivid example of how the past can be exploited by political powers. Used as a part of propaganda, which fueled the war, history can become a weapon in the hands of those who want to use it for their own goals.
And this is what humans have been doing since the dawn of time. There is always someone who will use any means necessary to achieve whatever it is they wish. This results in wars and genocides, and hundreds of smaller but no less devastating tragedies.
Therefore, the problem isn’t whether people should be learning history but human nature itself. Perhaps, teaching this can help fix this fundamental flaw and truly stop the worst of the past from repeating.
-

 Business11 months ago
Business11 months agoHow To Future-Proof Your Business With The Right Tools
-

 Travel9 months ago
Travel9 months agoTravelling from San Antonio to Guadalajara
-

 Business12 months ago
Business12 months agoWhat are EDC products, and why should you always have them?
-

 Travel6 months ago
Travel6 months agoTravel wellness tips for a healthier and more enjoyable journey
-

 Europe4 months ago
Europe4 months agoRecent Books by Boaventura de Sousa Santos: Law, Colonialism, and the Future of Europe